Acesta e primul articol pe care va recomand sa nu-l cititi in intregime ci dimpotriva, sa cititi primele randuri, sa actionati in consecinta si apoi sa reveniti sa-l terminati de citit.
Pe scurt, daca aveti linux instalat pe un server/desktop FACETI URGENT UPGRADE LA BASH!!!
Ok, acum ca v-ati facut deja upgrade la bash, o sa va dau cateva detalii tehnice legate de acest exploit.
Bash-ul suporta atat exportul de variabile shell cat si de functii shell intre instante diferite via environment catre procesele copii (child processes). Versiunile curente de bash utilizeaza o variabila de environment denumita dupa numele funtiei iar functia incepe cu “() {” in valoarea variabilei pentru a propaga continutul functiei catre enviroment.
De exemplu, daca setam o variabila de enviroment
VAR=() { ignored; }; /bin/script
se va executa /bin/script cand environment-ul e importat in bash si raul a fost deja facut.
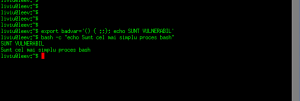
Iata cum arata un bash vulnerabil si unul updatat acum cateva minute:
ASA NU E OK:
liviu@xxx:$ export badvar='() { :;}; echo SUNT VULNERABIL'
liviu@xxx:$ bash -c "echo Sunt cel mai simplu proces bash"
SUNT VULNERABIL <<< ASTA NU AR TREBUI SA APARA !!!
Sunt cel mai simplu proces bash
ASA E OK:
liviu@xxx:$ export badvar='() { :;}; echo SUNT VULNERABIL'
liviu@xxx:$ bash -c "echo Sunt cel mai simplu proces bash"
bash: warning: badvar: ignoring function definition attempt
bash: error importing function definition for `badvar'
Sunt cel mai simplu proces bash
O sa revin cu niste exemple concrete, pana atunci faceti UPGRADE LA BASH!
CUM SE POATE EXPLOATA VIA HTTP (ma gandesc cu groaza la toate firmware-urile de CPE-uri care folosesc CGI-uri):
So far, HTTP requests to CGI scripts have been identified as the major
attack vector.
A typical HTTP request looks like this:
GET /path?query-param-name=query-param-value HTTP/1.1
Host: http://www.example.com
Custom: custom-header-value
The CGI specification maps all parts to environment variables. With
Apache httpd, the magic string “() {” can appear in these places:
* Host (“www.example.com”, as REMOTE_HOST)
* Header value (“custom-header-value”, as HTTP_CUSTOM in this example)
* Server protocol (“HTTP/1.1”, as SERVER_PROTOCOL)
The user name embedded in an Authorization header could be a vector as
well, but the corresponding REMOTE_USER variable is only set if the
user name corresponds to a known account according to the
authentication configuration, and a configuration which accepts the
magic string appears somewhat unlikely.
In addition, with other CGI implementations, the request method
(“GET”), path (“/path”) and query string
(“query-param-name=query-param-value”) may be vectors, and it is
conceivable for “query-param-value” as well, and perhaps even
“query-param-name”.
SURSA: http://seclists.org/oss-sec/2014/q3/649
CUM SE POATE EXPLOATA VIA SSH:
I’ve just confirmed that the issue can be exploited via OpenSSH setting
SSH_ORIGINAL_COMMAND:
$ ssh -o ‘rsaauthentication yes’ 0 ‘() { ignored; }; /usr/bin/id’
uid=500(sandbox) gid=500(sandbox) groups=500(sandbox)
Received disconnect from 127.0.0.1: Command terminated on signal 11.
This is with command=”set” in .ssh/authorized_keys for the key being
used. (Without the “; /usr/bin/id” portion, the command prints the
environment variables, including SSH_ORIGINAL_COMMAND being the function
with just “ignored” in its body.) As we can see, the command runs, and
moreover in this case bash happened to segfault after having run “id”.
SURSA: http://seclists.org/oss-sec/2014/q3/649